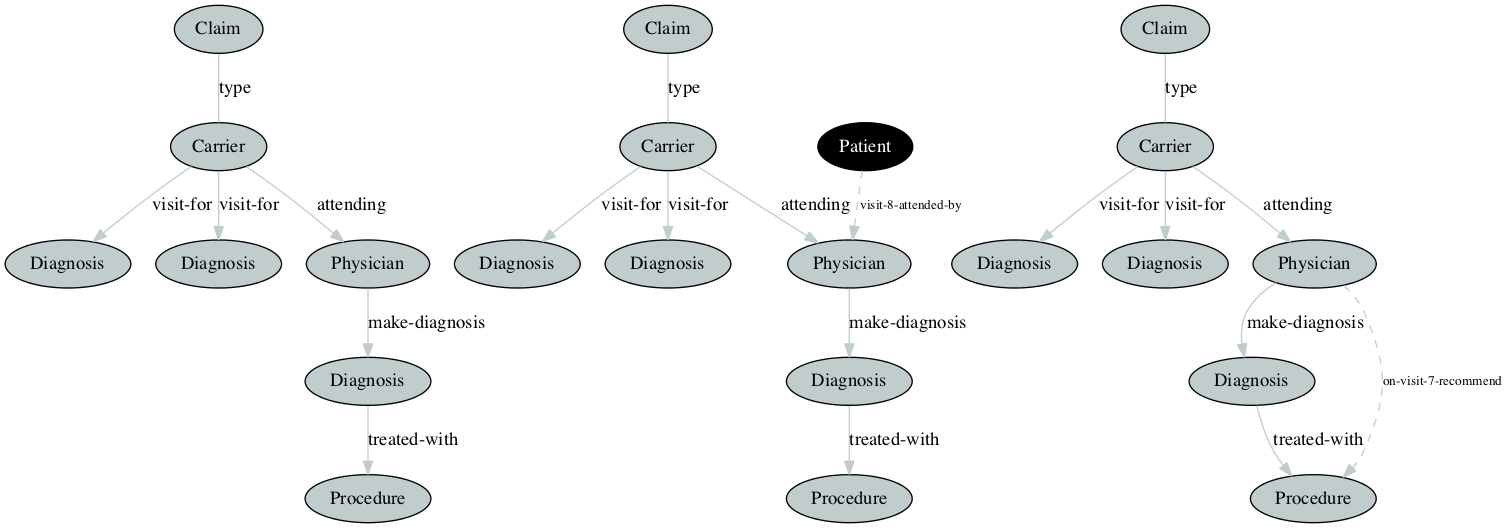
Detection of Anomalous Activity in Diabetic Patients
Every year, billions of dollars are lost due to fraud in the U.S. health care system. Health care claims are complex as they involve multiple parties including service providers, insurance subscribers, and insurance carriers. Medicare is susceptible to fraud because of this complexity. To build a comprehensive fraud detection system, one must take into consideration all of the financial practices involved among the associated parties. Various types of health-care fraud schemes are briefly described as follows:
- Identity Theft: Stealing identification information from providers or beneficiaries and using that information to submit fraudulent bills to Medicare.
- Phantom Billing: Billing for services that are not actually performed.
- Unbundling: Billing each stage of a procedure as if it were a separate treatment.
- Upcoding: Billing costlier services than the performed.
- Bill Padding: Providing medically excessive or unnecessary services to a patient.
- Duplicate Billing: Submitting same claims multiple times
- Kickbacks: A negotiated bribery in which a commission is paid to the bribe-taker (provider or patient) as a quid pro quo for services rendered.
- Doctor shopping: Patient consults many physicians in order to obtain multiple prescriptions of drugs in excess of their own therapeutic need.
This work is focused on graph-based analysis of CMS provided Medicare claims data to look for above anomalies by analysing the relationships and transactions among patients, service providers, claims, physicians, diagnosis, and procedures. In our experiments, we create graphs from inpatient, outpatient, and carrier claims data of the beneficiary. We then demonstrate the potential effectiveness of applying graph-based anomaly detection to the problem of discovering anomalies and potential fraud scenarios. For details please refer the paper published at FLAIRS-30 Conference Preceeding